Every industrial manufacturing conference you attend highlights all the possible business benefits and workloads associated with Industry 4.0: the convergence of operational technology (OT) and information technology (IT). Benefits that are often mentioned include: Click here to view original web page at www.netapp.com
Why Hybrid Cloud Security is the Future
The cloud is a fantastic way to deliver a multitude of services, but it’s equally important to recognize when a purely cloud approach can be sub-optimal. That’s why Harmony SASE takes a hybrid route. Our secure Internet Access offering provides on-device protection, while still providing functionality in the cloud for those who want it. That result is an internet security solution that keeps your workforce protected from online threats and maintains your connection speeds without negatively impacting device performance […] Click here to view original web page at www.checkpoint.com
Stay Compliant: Cisco Secure Workload Introduces State-of-the-art, Persona-based Reporting
Workload security tools draw the attention of diverse cohorts, united by a mission: fortifying hybrid cloud workloads. In a market filled with disparate tools, Secure Workload offers a tailored reporting solution that revolutionizes how SecOps, Network Administrators, and CxOs interact with their workload security solution […] Click here to view original web page at www.cisco.com
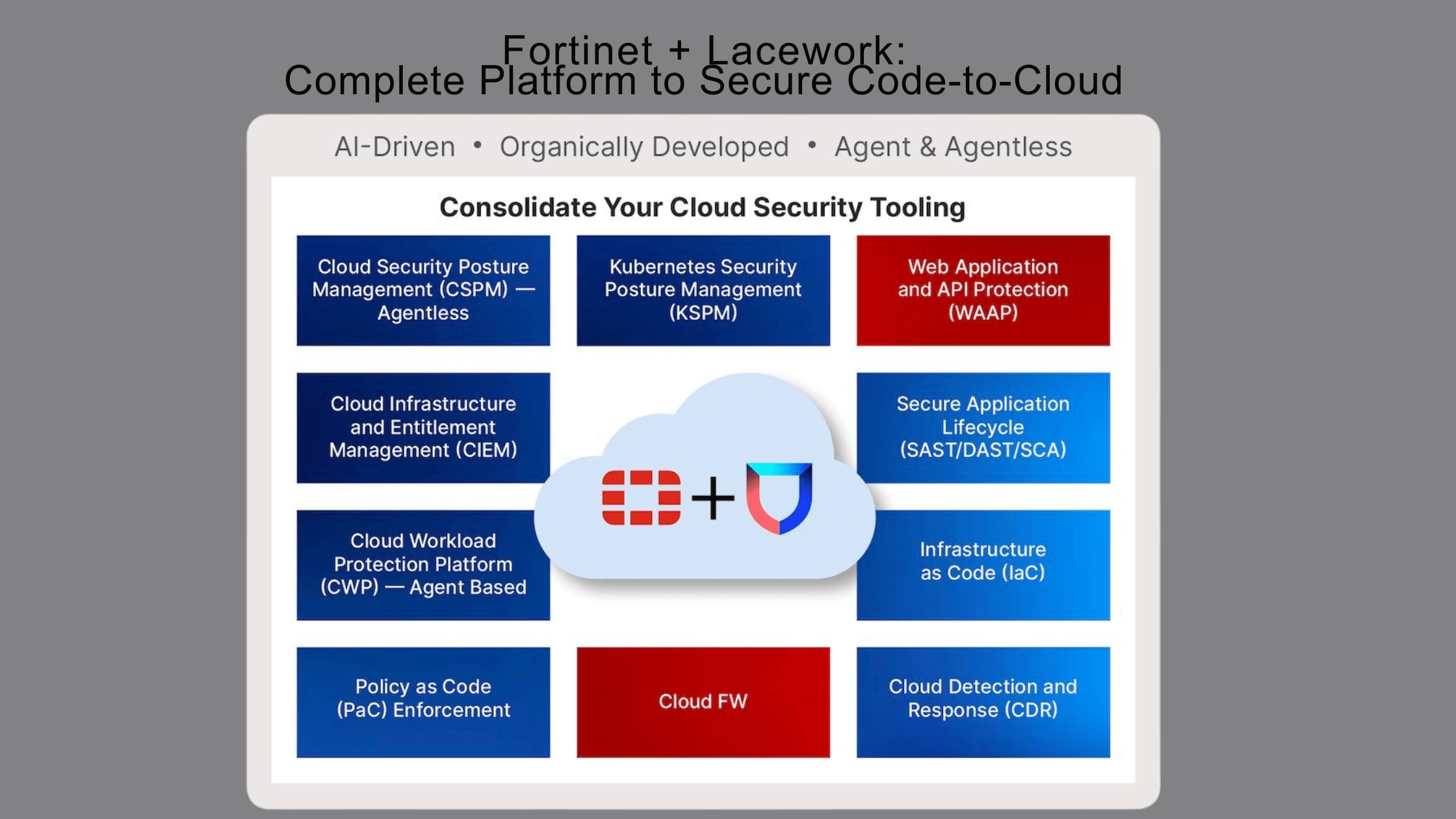
Adding an Advanced AI-Powered Cloud Native Security Platform to the Fortinet Security Fabric
Most customers will have hybrid infrastructure for the foreseeable future. Users are moving in and out of the office, more IoT and OT devices are connected, networks have more edges to protect, and applications are on a continuous journey across data centers, clouds, and SaaS. Cloud-native applications have gained popularity in recent years as a way of bringing applications to market more rapidly. While cloud-native environments offer more flexibility to enable rapid application development, they also pose a significant security challenge. The dynamic nature of the cloud-native paradigm widens the attack surface, leaving organizations vulnerable. As a result, there are numerous challenges when trying to secure […] Click here to view original web page at www.fortinet.com
Commvault Cloud for Government Is Now FedRAMP High Authorized
In today’s digital landscape, ensuring the security and compliance of sensitive data is of paramount importance, especially for government organizations. Commvault recognizes this critical need and has achieved a significant milestone by obtaining FedRAMP® High authorization for its Commvault® Cloud for Government, SaaS enterprise-grade data protection solutions […] Click here to view original web page at www.commvault.com
Turnkey AI-ready stack with FlexPod AI
The ready-to-use AI-ready stack featuring FlexPod® AI is designed to meet the needs of enterprise generative AI (GenAI) applications. It combines Cisco computing power, NetApp® storage solutions, NVIDIA GPUs, and a range of AI software to create a validated infrastructure platform that enables businesses to develop and implement custom chatbots, virtual assistants, and applications through retrieval-augmented generation (RAG) technology […] Click here to view original web page at www.netapp.com
Cisco API Documentations Is Now Adapted for Gen AI Technologies
Developer experience changes rapidly. Many developers and the Cisco DevNet community utilize Generative AI tools and language models for code generation and troubleshooting. In the article, “How To Get Started Using LLMs in IT and Network Engineering,” we discussed result of how our community utilized LLMs. Better data = better model completion The main challenge for GenAI users is finding valid data for their prompts or Vector Databases. Developers and engineers need to care about the data they plan to use for LLMs/GenAI interaction […] Click here to view original web page at www.cisco.com
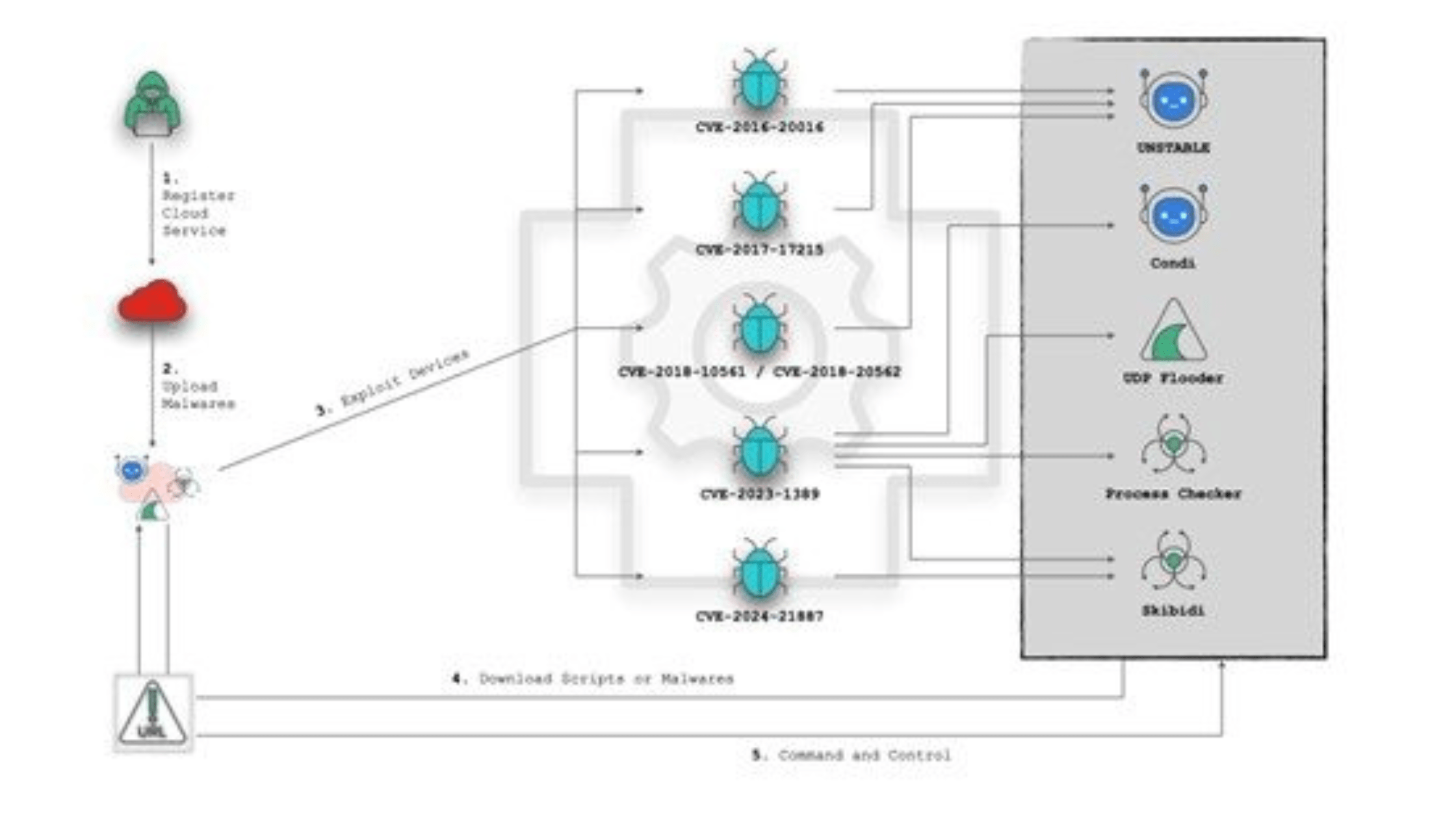
The Growing Threat of Malware Concealed Behind Cloud Services
Cybersecurity threats are increasingly leveraging cloud services to store, distribute, and establish command and control (C2) servers, such as VCRUMS stored on AWS or SYK Crypter distributed via DriveHQ. This shift in strategy presents significant challenges for detection and prevention, as cloud services provide scalability, anonymity, and resilience that traditional hosting methods lack. Over the past month, FortiGuard Labs has been monitoring botnets that have adopted this strategy, abusing cloud services to enhance their malicious capabilities. These botnets, such as UNSTABLE and Condi, have been observed leveraging cloud storage and computing services operators to distribute malware payloads and updates to a broad range of devices […] Click here to view original web page at www.fortinet.com
Data protection is important; data recovery is critical
In our connected world, the widespread adoption of technology has revolutionized the way organizations deliver data-based services. Whether it’s consumers relying on online platforms or governments serving citizens, the importance of data—the lifeblood of these services—cannot be overstated. Protecting this data is paramount, because any malicious access leading to its modification, theft, encryption, or deletion can result in catastrophic consequences with a profound societal impact […] Click here to view original web page at www.netapp.com
How ThreatCloud AI’s Threat Emulation Engine Prevents DLL Sideloading (Trojan) Attacks
A sophisticated new malware/trojan attack is designed to steal login credentials and credit card information from payment systems, banks and crypto exchanges. This attack tricks legitimate business applications into running compromised but innocent-looking dynamic link library (DLL) files — making it very difficult to detect and block. DLL sideloading is a technique used by cybercriminals to execute malicious code on a target system by exploiting the way Windows loads dynamic link libraries (DLLs). This blog explores how Check Point’s advanced Threat Emulation engines, part of Infinity ThreatCloud AI, detected and prevented a DLL Sideloading attack on one of our customers. Click here to view original web page at www.checkpoint.com