In the last few hours, major disruptions on CrowdStrike’s Falcon platform causing significant productivity impacts due to inaccessible documents have been reported. The CrowdStrike Falcon update has led to a “blue screen of death” globally, severely impacting business operations dependent on this technology. This issue requires immediate attention to mitigate potential system failures […] Click here to view original web page at www.checkpoint.com
Unified data storage and the art of balancing data center modernization with the benefits of the cloud
Getting ahead in a world where disruption is the norm requires seamless access to data, no matter where it lives. Cloud is no longer a separate IT initiative, but often, organizations fear the costs and complexities associated with modernizing and managing data across on-premises and cloud environments. And these fears can hold you back from realizing the full potential of your data. Data storage modernization should reduce the complexity compounded by silos and deliver the performance, reliability, mobility, security, and scalability that you need […] Click here to view original web page at www.netapp.com
Generative AI: Reshaping the Telecoms Landscape – Part 1
In recent years, the telecommunications industry has been at the forefront of adopting cutting-edge technologies to enhance operational efficiency, improve customer service, and innovate in service offerings. Now, the industry is undergoing a profound transformation. One of the most transformative technologies driving this evolution is Generative Artificial Intelligence (Gen AI). Gen AI represents a significant leap from traditional AI systems, as it aims to replicate human-like cognitive abilities, including reasoning, learning, and problem-solving. […] Click here to view original web page at www.huawei.com
Protecting Against regreSSHion with Secure Workload
On July 1, 2024, the Qualys Threat Research Unit (TRU) disclosed an unauthenticated, remote code execution vulnerability that affects the OpenSSH server (sshd) in glibc-based Linux systems. [For more information visit Qualys Security Advisory and our Cisco Security Advisory on regreSSHion (July 2024).] Now we have seen how CVE-2024-6387 has taken the internet by storm, making network security teams scramble to protect the networks while app owners patch their systems […] Click here to view original web page at www.cisco.com
Lenovo takes customer satisfaction to new heights with e-services enhanced by generative AI
Solving customer issues quickly, accurately and effectively on a global scale with new GenAI tools powered by GPT-4 Lenovo’s AI solution helps human experts improve the speed, accuracy and quality of interactions with customers on global support forums. The technology also enhances two existing customer-facing chatbots, enabling them to offer more human-like interactions and help with a wider range of support issues […] Click here to view original web page at www.lenovo.com
Cybersecurity and cyber resilience…aren’t they the same thing?
You probably hear the terms “cybersecurity” and “cyber resilience” used quite a bit, especially as cyberthreats become increasingly common—and costly. These terms don’t describe exactly the same thing, and there are a lot of misconceptions about the differences between them. So let’s make sure that we’re all on the same page. Why the difference matters Cybersecurity is a pretty broad term, but it generally refers to system defenses that protect against unauthorized access from attackers […] Click here to view original web page at www.netapp.com
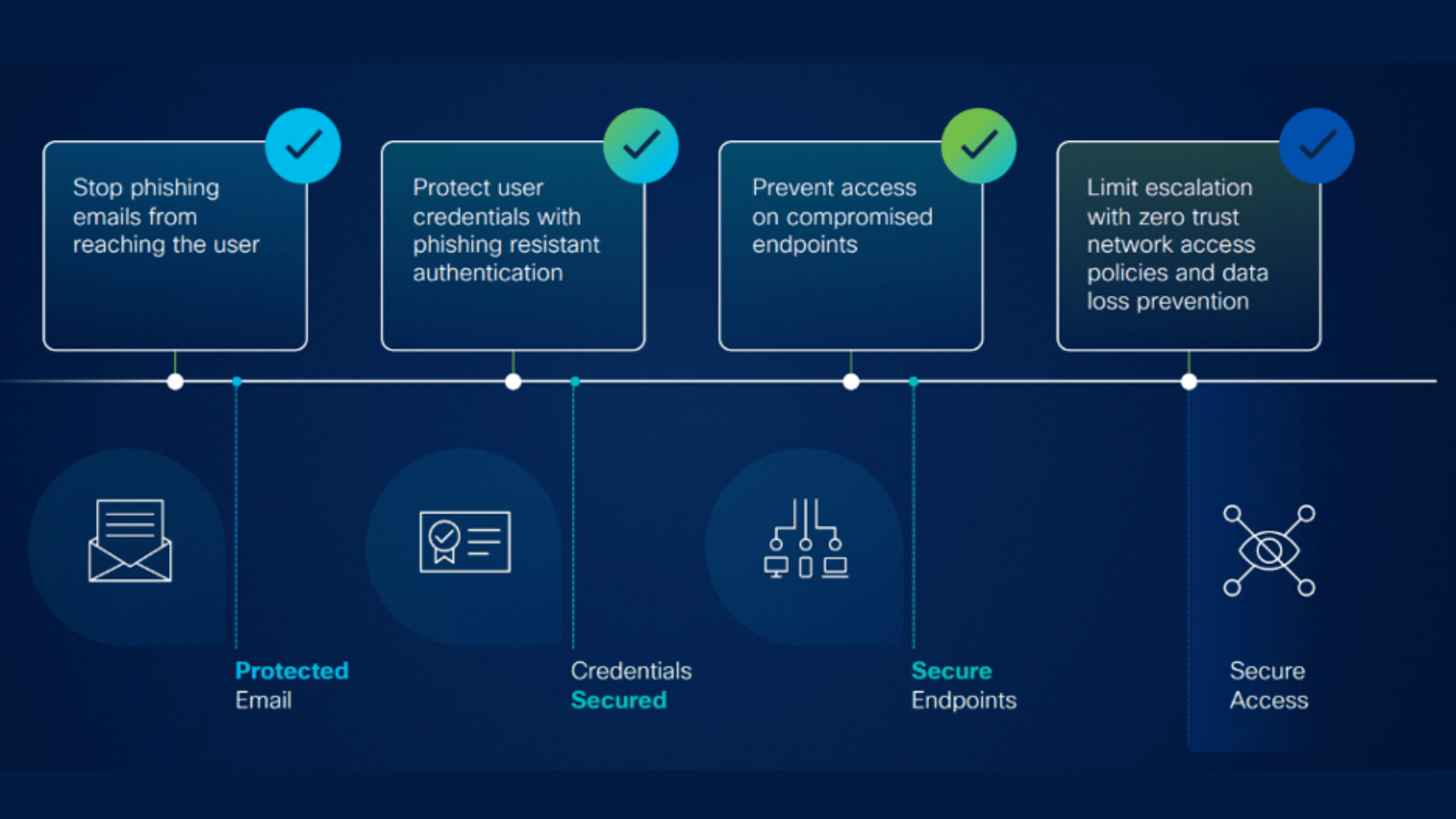
Stopping Supply Chain Attacks with Cisco’s User Protection Suite
The Dinner Party Supply Chain Attack A supply chain attack occurs when a bad actor gains access to an organization’s people and data by compromising a vendor or business partner. Let’s think of this type of attack as if it was a dinner party. You invite your close friends over and hire a catering company that you know and trust to cook the meal. However, neither you nor the caterer were aware that one of the waiters serving your guests stole the key to your house and made a copy. You throw a lovely party, and your friends rave about the food, and everyone goes home. But later that week you come home to find all your valuables missing […] Click here to view original web page at www.cisco.com
AI-Ready Data Infrastructure: Transforming Industries
AI is going from strength to strength and is beginning to spur transformative change in industries from finance to healthcare to education and beyond. A sort of rhythm has been established—a leading player announces the latest feat of its AI model, and no sooner have we retrieved our jaws from the floor, we are presented with another announcement, this time of feats more impressive still […] Click here to view original web page at www.huawei.com
When you realize that it’s more about data than about storage
We recently hosted the annual NetApp Industry Analyst Summit in New York City, bringing together some of the best thinkers in our industry. In one session about the incredible amount of data hitting us all from the AI tsunami, one brilliant-but-blunt participant said, “It’s a good time to be in the storage business.” That I can’t deny; but is it a good time to be dependent on these storage farms? The answer may be more about how much intelligence you’ve put into managing that exploding data stockpile than about the storage itself […] Click here to view original web page at www.netapp.com
New Layers of Data Defense: Multi-person Authorization & Compliance Lock
As evident with Commvault’s recent Secure by Design Pledge, we are committed to providing our customers with a secure platform to help manage risk and remain resilient in today’s digital landscape. n the ever-evolving cybersecurity space, threats are becoming more sophisticated and widespread. Securing privileged access has emerged as a critical imperative for organizations. Privileged access refers to elevated permissions and rights granted to certain users or accounts within an IT environment, often with the ability to delete, edit, reconfigure, or destroy parts of infrastructure or data […] Click here to view original web page at www.commvault.com